Today we are rolling out a new firmware update for Atola flagship product! While 2020.7.1 is considered a minor update, the new RAID and connectivity features are numerous and substantial. They will facilitate TaskForce’s connectivity capabilities and enhances autodetection of RAID arrays, the feature initially introduced in 2020.7.
RAID features
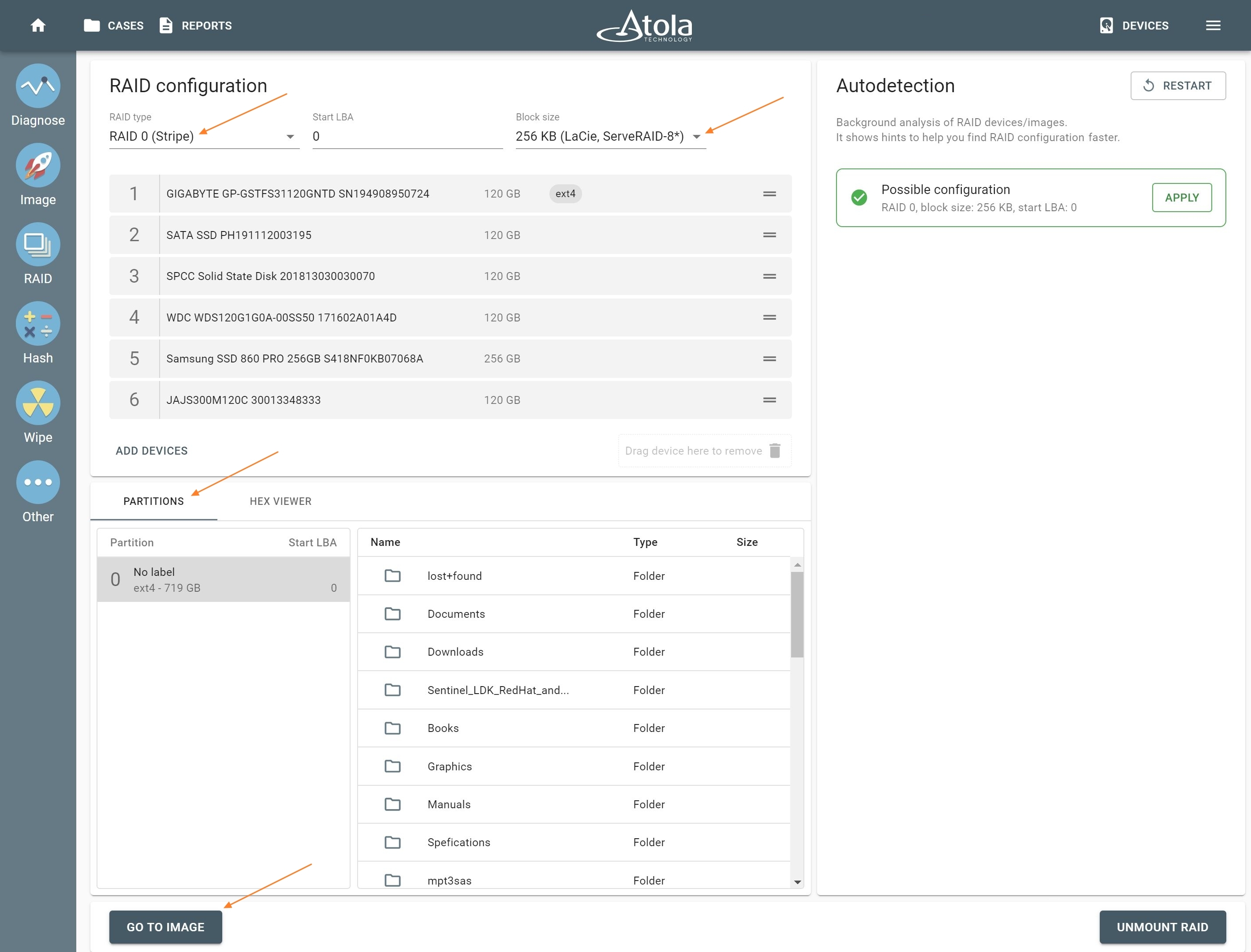
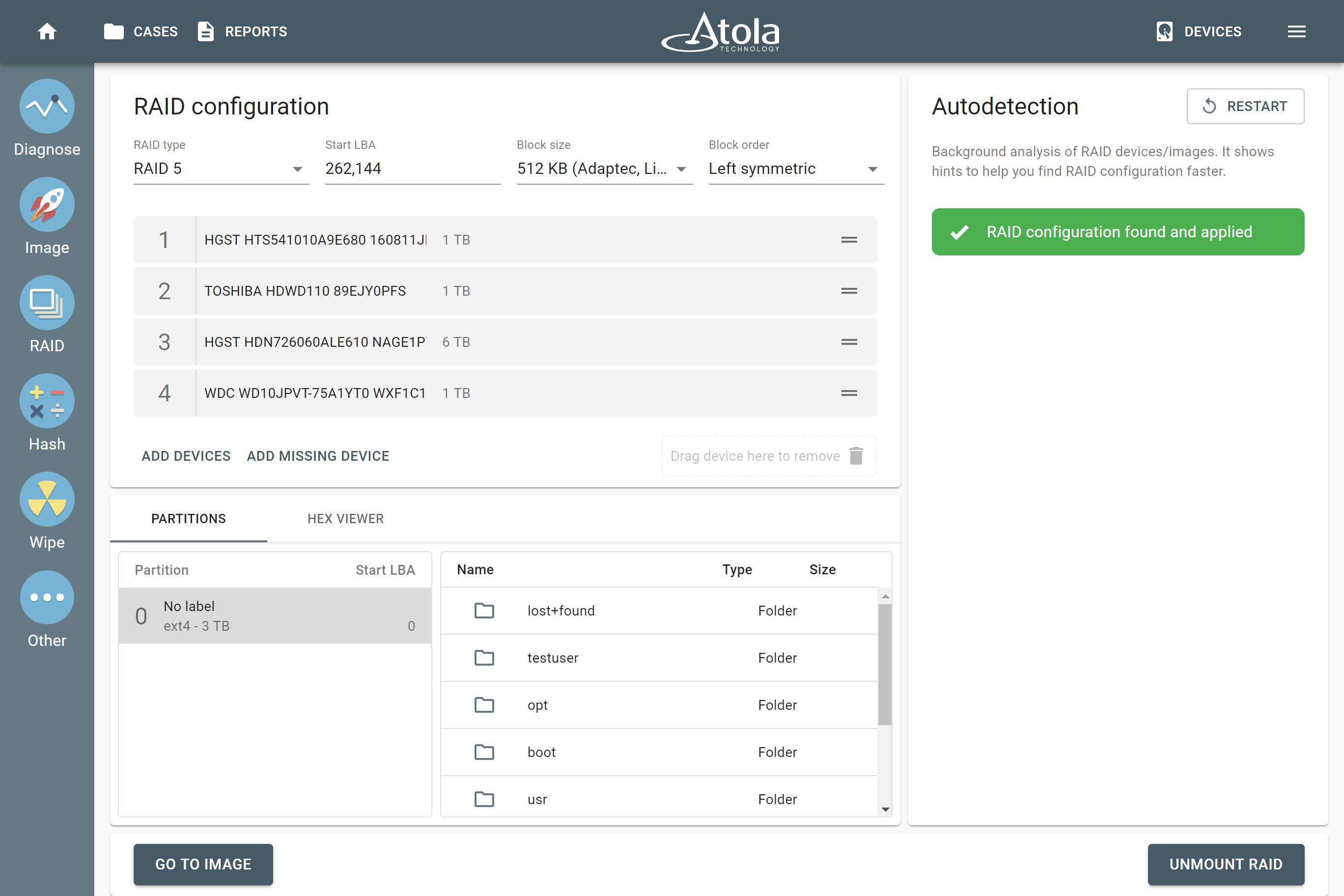
In v 2020.7 you might have seen an output of a multitude of detected possible configurations for a RAID array. The new 2020.7.1 firmware equips the RAID autodetection module with a more effective algorithm for file system validation. In 90+% of such cases, autodetection will narrow it down to a single possible RAID configuration!
The maximum number of autochecked configurations has been increased from 500,000 to 100,000,000.

This seemingly minor change allows accommodating cases with 8+ devices with complex configurations.
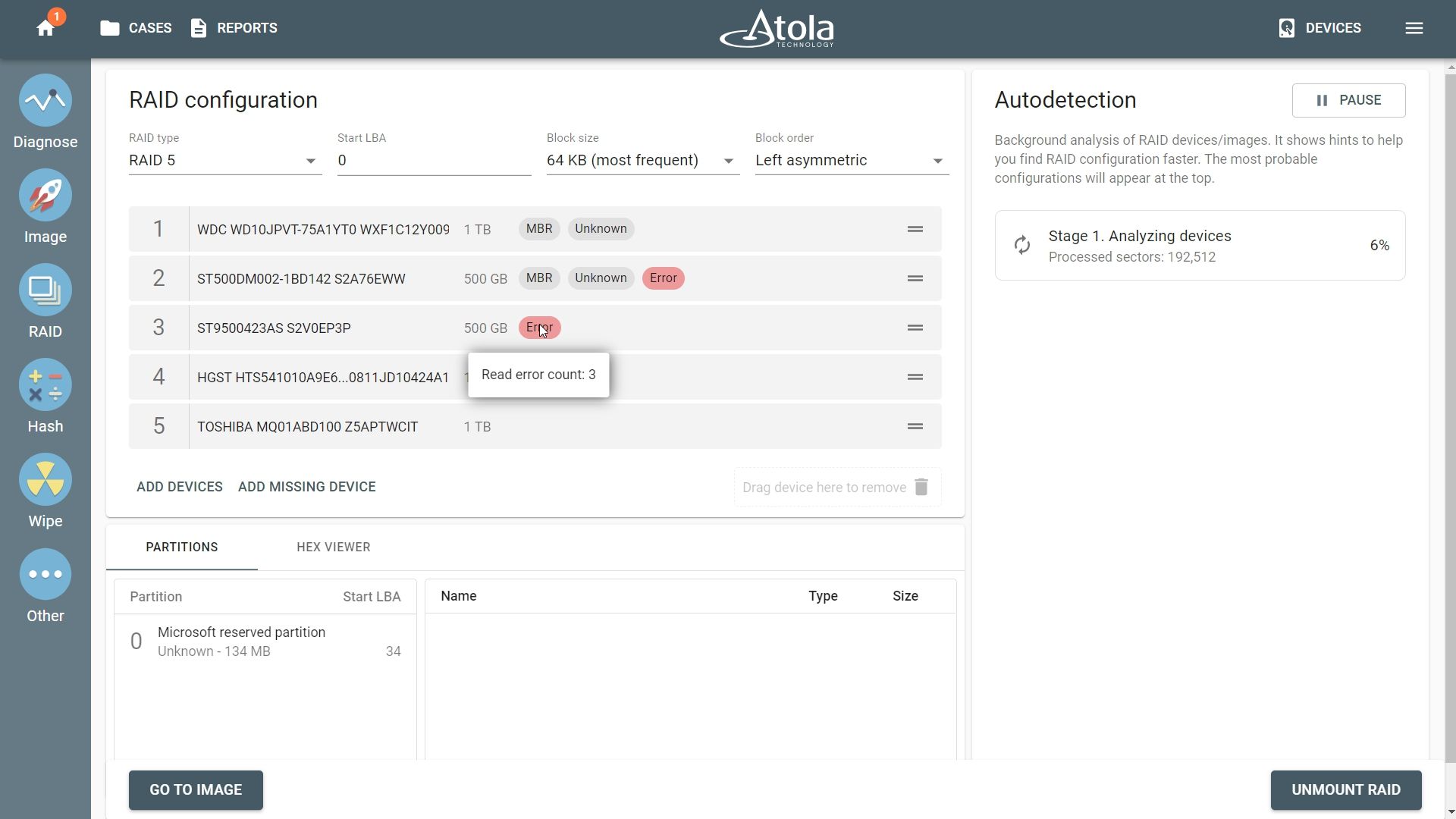
The number of variants to be checked for RAID arrays with 8+ devices can reach a few million. For example, a RAID 5 consisting of 8 drives would not have covered all the possible configurations in 2020.7 version but will work in 2020.7.1 due to the previous limit of 500,000 configurations:
For such RAID 5 arrays, TaskForce has to go through 12 block size variants, 4 possible block order variants and 8! (8 factorial for the order of the 8 devices included in the RAID), which adds up to 1,935,360 overall variants.
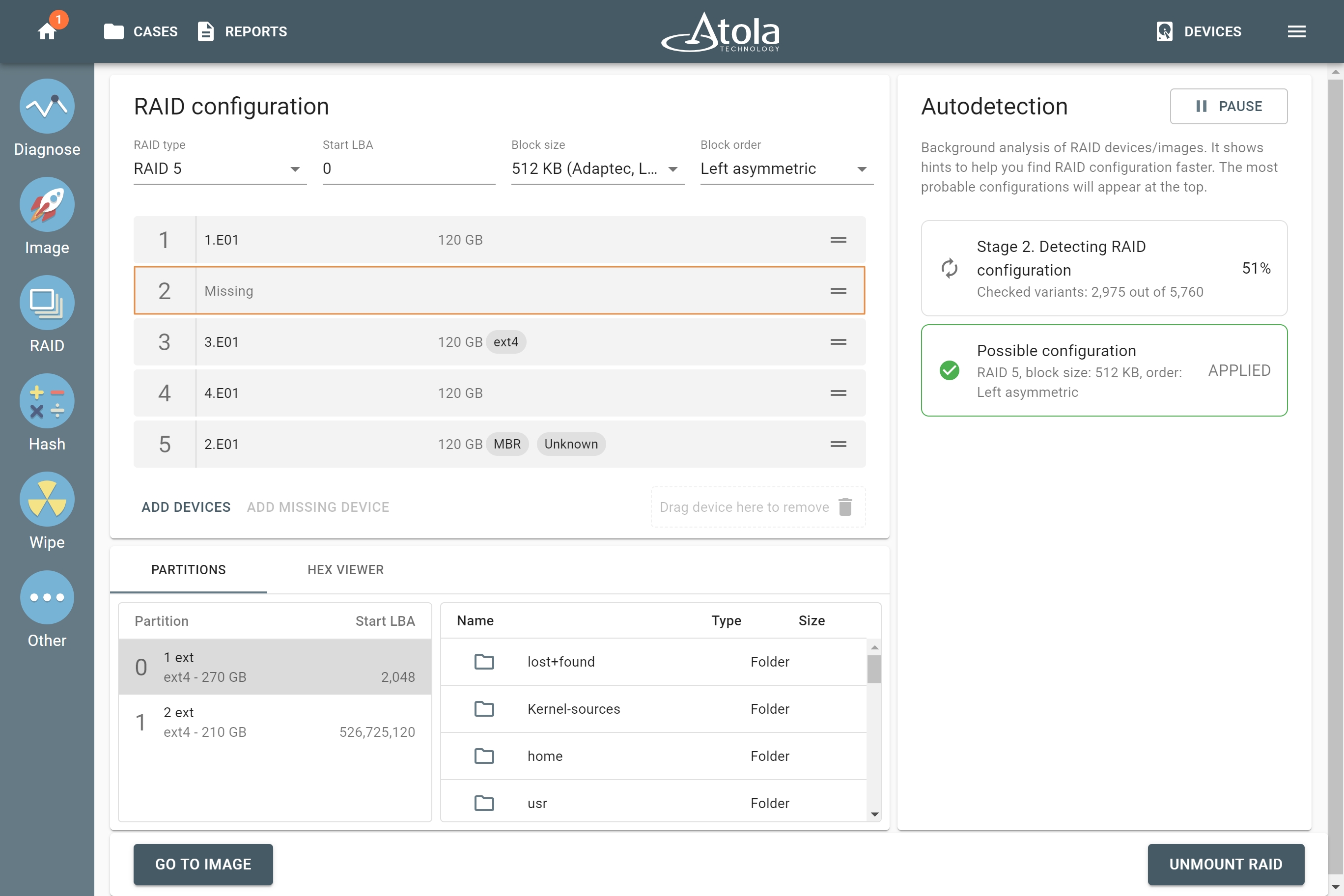
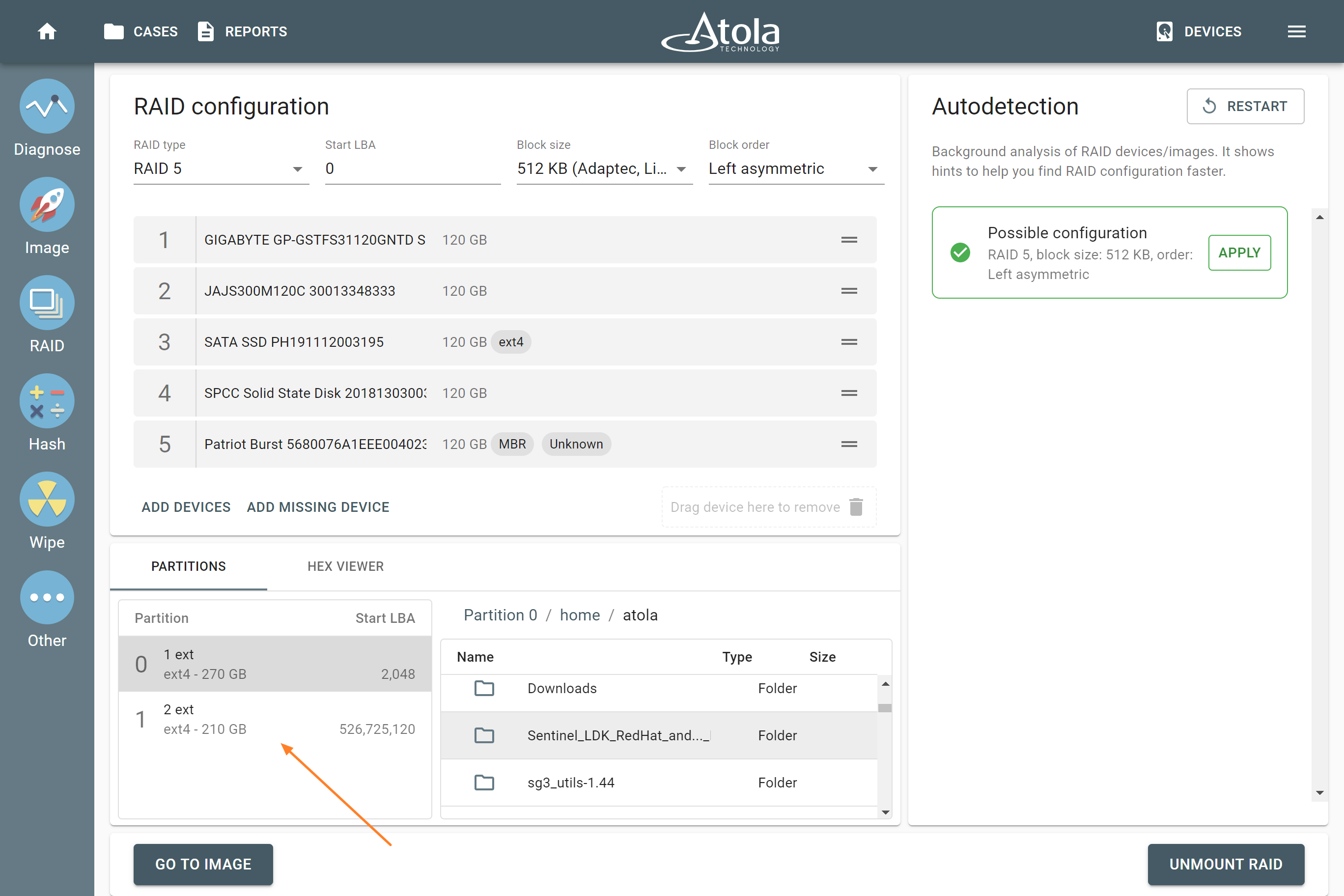
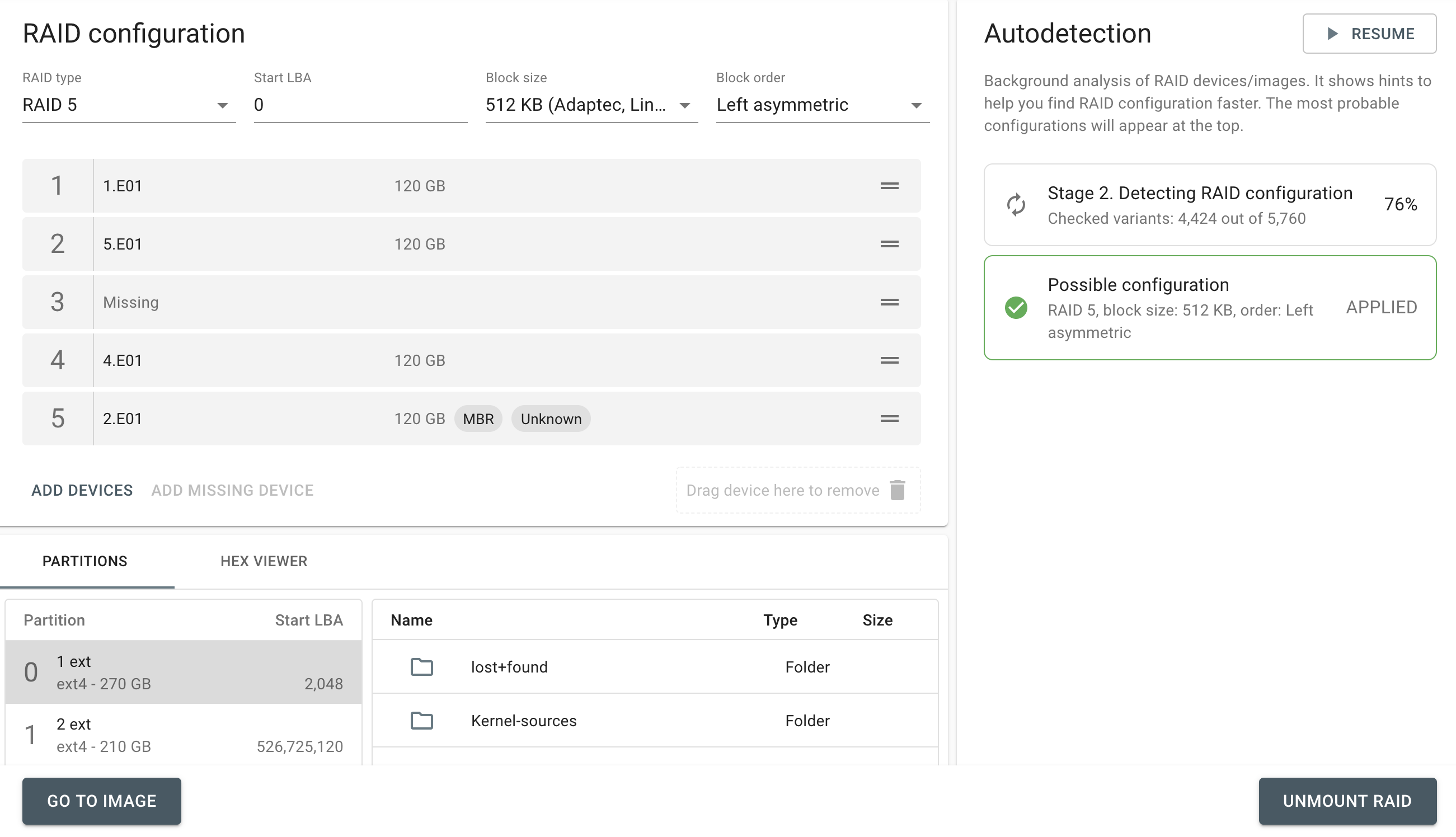
RAID 5. Adding Missing Device starts a new RAID autodetection
If you are trying to mount a RAID array, that is likely a RAID 5, and there is a damaged or missing device in the array, you can use the Missing Device button to add a virtual device. The moment you do that, Autodetection restarts and runs through all possible variants from scratch. This new search takes into consideration a missing device, taking advantage of the parity of the RAID 5 array.
Connectivity features
New network settings for an easier TaskForce configuration in an organization’s network: DNS nameserver, Default gateway.

Connect dialog allows specifying a full network folder path to facilitate access to folders on a server.

2020.7.1 changelog
New Features
RAID:
- Improved RAID autodetection. Fine-tuned algorithms to narrow the possible configurations down to a single variant more frequently.
- When multiple RAID assumptions are suggested, they are listed in the order of probability
- New Error tag is displayed if read errors are encountered during RAID autodetection. The tag’s tooltip shows read error count.
- Improved handling of a damaged drive when one of RAID devices freezes while reading sectors
- Memory use optimized for RAID autodetection involving more than 8 devices
- Maximum number of autochecked configurations increased from 500,000 to 100,000,000
- RAID 5. Ability to add a Missing Device and start another RAID autodetection
- RAID 5 based on mdadm. Automatic addition of a Missing Device.
- Summary hint with recommendations is shown if RAID autodetection failed to find the right RAID configuration
Network setup + Imaging to server:
- DFS (Distributed File System) supported
- Connect dialog allows specifying a full network folder path
- New network settings: DNS nameserver, Default gateway
- Ability to work in networks having SMBv2 strictly disabled
Bugfixes
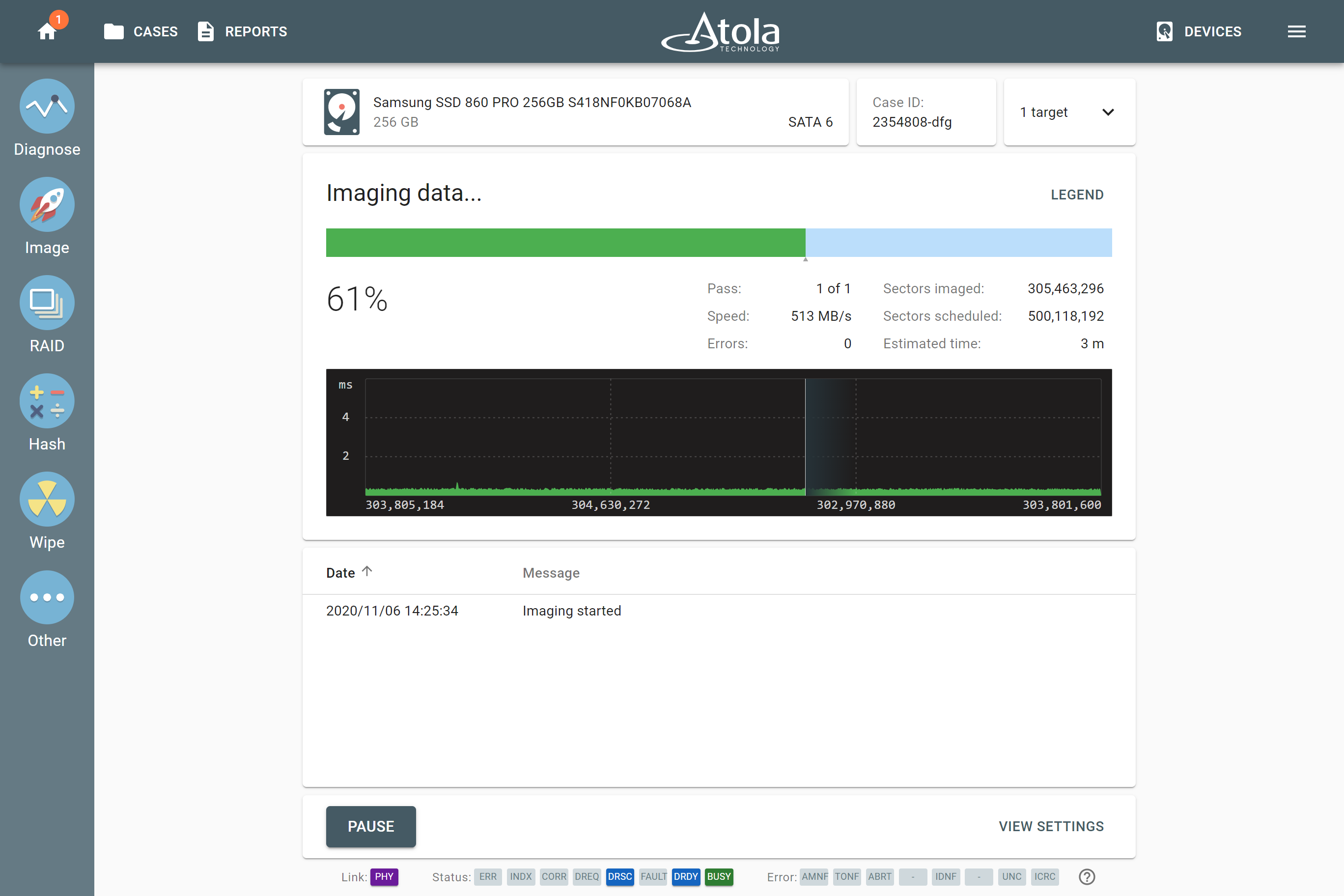
Imaging:
- The following message was missing in the imaging log: Source device HPA was set to native max address until power cycle: 123,123,123
- Imaging could not be started if limiting the target device to source size by HPA failed
- Rare imaging interruption when attempting to start selective head imaging with some models of Toshiba drives
- Imaging (Hashing, Wiping, as well) could not be started against NetAPP SAS drives
- Disable read-look ahead setting was not working properly
- Resuming imaging for RAID wasn’t possible after pausing imaging and changing the RAID configuration
Other fixes:
- RAID. Serial numbers of selected devices were not always entirely visible on RAID configuration page
- RAID. Add devices buttons and Remove device area missing when using screen tablet with 6+ devices selected
- Storage drive automounting now works in Target mode only. Previously, it was running for both Source and Target modes.
- Fixed a few minor issues with case reports created for RAID devices
- Case import completed report might have no detailed information inside
Download
You can download the latest update here: TaskForce firmware
Where to buy
If you still do not have an Atola TaskForce and would like to place an order, this can be done directly via Atola Technology, or from a distributor near you:
Please contact Atola Technology sales department to receive more specific information:
- Call us: +1 888 540-2010, +1 416 833-3501 10am – 6pm ET
- Or email us
P.S. Dear customers, we appreciate your feedback and take it into consideration when updating our products. Please feel free to write your thoughts and ideas in the comments section below.
The post Atola TaskForce 2020.7.1 introduces RAID and connectivity features appeared first on Atola Technology.